Sophos Utm 9.7
Fastvue Sophos Reporter consumes syslog data from Sophos UTM (SG) and Sophos XG Firewalls and produces clean, simple, web usage reports that you can confidently send to department managers and HR team. Automate reports and get the job of reporting on web usage off your desk and into the hands of people that need it. The Sophos UTM Free Home Use firewall contains its own operating system and will overwrite all data on the computer during the installation process. Therefore, a separate, dedicated computer is needed, which will change into a fully functional security appliance.
Configuration the Sophos UTM is easy in 12 steps. This perform basic setup for a computer in LAN go out internet through UTM.
Important Step noted:
- Setup WAN interface and Default Gateway (step 6)
- Setup DNS forwarder (step 7)
- Setup Firewall Rule (step 8)
- Setup NAT Masquerading (step 9)
- Option for setup DHCP server
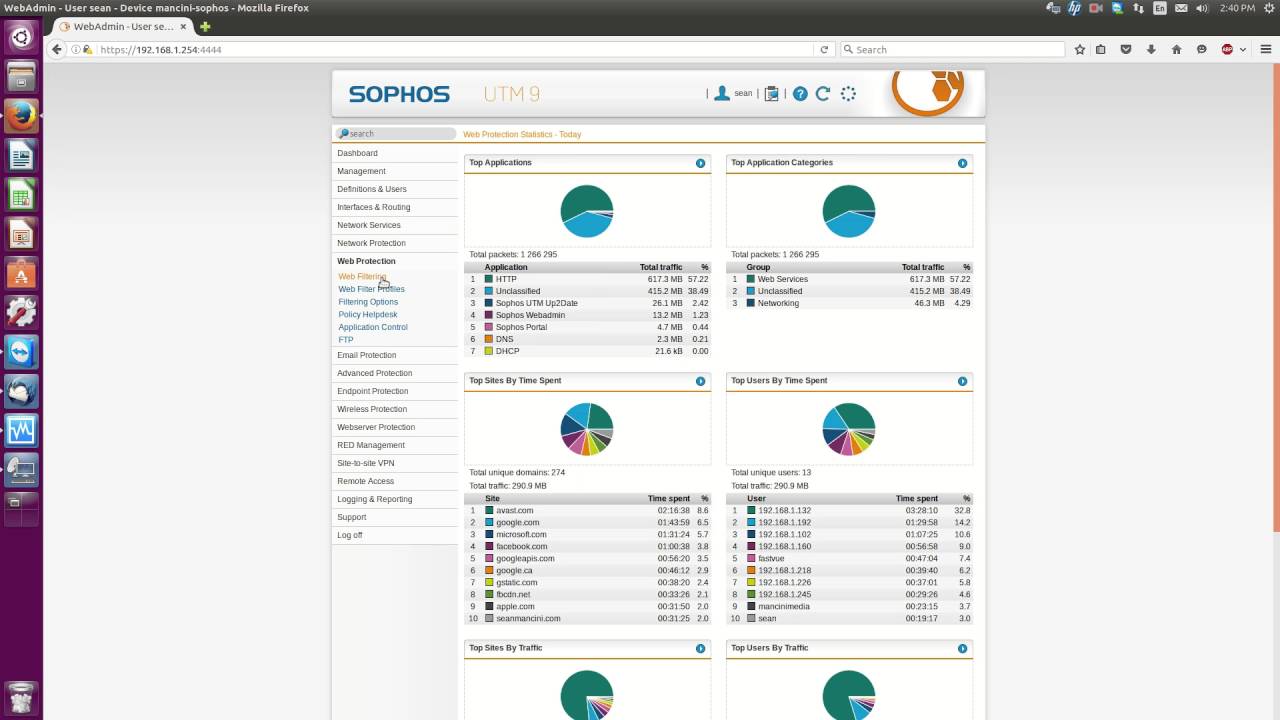
STEP 1: Go to Webadmin by default IP address:
Sophos UTM hardware default IP: https://192.168.0.1:4444
Sophos UTM Software default IP: https://192.168.2.100:4444
In this example: https://192.168.88.254:4444
See more in Sophos UTM Software/hardware Appliance Quick Start Guide

STEP 2: Enter Administrator Contact and Password
Click APPLY and waiting for some second
STEP 3: Go to again Webadmin with new certificate
You will be noticed the Certificate error, and Add Exception for this.
STEP 4: Login to Webadmin with new password
STEP 5: Cancel the Wizard
Click “Cancel” button in bottom of Wizard
You will see the dashboard of Sophos UTM
STEP 6: Add WAN Interface
Go to “Interfaces & Routing” -> “Interfaces” -> click “New Interface”
· Name: WAN
· Type: Ethernet
· Hardware: choose the hardware interface connect to Router/Modem of ISP
· IPv4 Default Gateway: Checked

Click “SAVE” and you will see the new interface which is disabled
Click enable button to enable the WAN Interface
STEP 7: Setup DNS
Add Google or Public DNS to DNS forwarders
STEP 8: Setup Firewall Rule
Go to Network Protection -> Firewall
Default No rule and all traffic is blocked.
Click New Rule Button
· Sources: Internal Network
· Services: ANY (or Some Services)
· Destinations: ANY
· Action: Allow
· Advanced: Log Traffic checked
Enable the new firewall Rule
STEP 9: NAT
Go to Network Protection -> NAT -> Masquerading
· Network: Internal (Network)
· Interface: WAN
· Use address: Primary address
Enable the new Masquerading Rule
STEP 10: Enable Advanced Threat Protection
Go to Network Protection -> Advanced Threat Protection -> Click Enable button (Grey to Green)
STEP 11: Enable Intrusion Prevention System
Go to Network Protection -> Intrusion Prevention -> Click Enable button (Grey button in the right).
Add the Internal (Network) to Local Network box -> Click Apply.
Enable Anti-Portscan
STEP 12: Check the Firewall Live Log
Go to Network Protection -> Firewall
Click “Open Live Log” button
· Green line: traffic allow through firewall
· Red line: traffic deny through firewall
Option STEP: DHCP Server (if needed)
Go to Network Services -> DHCP -> Click “New DHCP Server” button.
· Interface: Internal
Done!
Sophos has released UTM 9.7 as beta, it is a very small “new” UTM version, with a small number of features, sadly, but their focus is on XG now, and UTM is moving towards EOL, it is not announced yet though, here are the releases notes, but remember, it’s BETA 🙂 :
Support for new APX AcessPoints
In addition to the regular AP series access-points UTM 9.7 brings support for the new APX series access-points that can now also be added and managed with UTM 9. This includes support for APX 120, APX 320, APX 530 and APX 740.
Sophos Utm 9.7 Download
Certificate Chain support for WebAdmin and UserPortal
Full certificate chains that are uploaded to UTM for use with WebAdmin and/or UserPortal will no longer be split but will be delivered in full when accessing WebAdmin and/or UserPortal and web browsers will no longer display warnings for these certificates.
Certificate Chain Support for WebProxy
When using an intermediate certificate to sign HTTPS decryption certificates in WebProxy, WebProxy will now build and return a full certificate chain for the generated certificate to avoid browsers showing a warning when not explicitly trusting the intermediate certificate. The root certificate has to be available within the verification CAs.
New RED Site 2 Site Protocol
RED Site 2 Site connections in UTM will now use the same protocol used within XG Firewall for RED Site 2 Site connections. This removes the need to specify legacy RED site 2 site connections in XG Firewall and provides enhancements to the RED site 2 site implementation in UTM.
Retirement of UTM Endpoint Management
As announced with UTM 9.6, UTM endpoint management will be end of life by the end of this year. UTM 9.7 will no longer include the option for Endpoint Management for the UTM Managed Endpoints, Sophos SEC integration is still part of UTM 9.7.
- NUTM-10804 [Access & Identity] strongSwan vulnerability fix (CVE-2010-2628, CVE-2018-17540)
- NUTM-10745 [Email] Quarantine mail older than 14 days are not getting removed
- NUTM-10958 [Email] Quarantined SPX Mails which are released are still available on UTM
- NUTM-10873 [WAF] Underscore in DNS-Hostname makes WAF unusable
| Up2Date package from current 9.605 to 9.7 EAP1 (9.670) | u2d-sys-9.605001-670004.tgz.gpg | MD5SUM: 9a16efcaf57bf6368d63adfa3a6b7f45 |
| Appliance ISO | ssi-9.670-4.1.iso (will be available soon) | MD5SUM: b536acb215ba085549afc283650fbd44 |
| Software ISO | asg-9.670-4.1.iso (will be available soon) | MD5SUM: f4888657550f6b7d83b33ae77997c6d0 |
You can use the license below for the beta phase: UTM-9.7-EAP-License
Sophos Utm 9.705-3
Up2Date 9.670004 package description:
Remarks:
System will be rebooted
Configuration will be upgraded
Connected REDs will perform firmware upgrade
Connected APs will perform firmware upgrade
News:
Feature Release
.
Support for new APX AccessPoints
Certificate Chain support for WebAdmin and UserPortal
Certificate Chain Support for WebProxy
New RED Site 2 Site Protocol
Retirement of UTM Endpoint Management
Sophos Utm 9.7 Download
Bugfixes:
Fix [NUTM-10804]: [Access & Identity] strongSwan vulnerability fix (CVE-2010-2628, CVE-2018-17540)
Fix [NUTM-10745]: [Email] Quarantine mail older than 14 days are not getting removed
Fix [NUTM-10958]: [Email] Quarantined SPX Mails which are released are still available on UTM
Fix [NUTM-10454]: [WAF] SAVI integration doesn’t support scanning files larger than 2GB
Fix [NUTM-10873]: [WAF] Underscore in DNS-Hostname makes WAF unusable
RPM packages contained:
libapr-util1-1.6.1-0.gd09a905.rb2.i686.rpm
libapr1-1.6.5-0.gdb882c9.rb2.i686.rpm
libsaviglue-9.70-35.g5c778eb.rb2.i686.rpm
cm-nextgen-agent-9.70-6.gac30f9d.rb2.i686.rpm
dehydrated-0.6.5-0.g6d4140c.rb2.i686.rpm
firmwares-bamboo-9400-0.328884155.gcf6a697.rb2.i586.rpm
hostapd-2.2-1.0.287145451.ga02be97.rb8.i686.rpm
modauthnzaua-9.70-270.gcb78b67.rb57.i686.rpm
modauthzblacklist-9.70-345.gb8b010d.rb9.i686.rpm
modavscan-9.70-359.g793e6f1.rb5.i686.rpm
modcookie-9.70-0.247140156.g8f24856.rb54.i686.rpm
modcustomblockpage-9.70-279.gbe16bc0.rb52.i686.rpm
modfirehose-2.5_SVNr1309567-14.g4ab2622.rb57.i686.rpm
modformhardening-9.70-252.g1471b81.rb62.i686.rpm
modpcap-9.70-0.142961807.g994d6f0.rb57.i686.rpm
modproxymsrpc-0.5-121.gc7f8565.rb65.i686.rpm
modproxyprotocol-0.1-30.gac71dfd.rb29.i686.rpm
modreverseauth-9.70-0.253882348.g852e9e5.rb59.i686.rpm
modsecurity2-2.9.1-266.g649c52a.rb61.i686.rpm
modsecurity2_beta-2.9.0-460.g62b8fdb.rb61.i686.rpm
modsessionserver-9.70-0.247653793.g4179dcf.rb60.i686.rpm
modurlhardening-9.70-252.g1471b81.rb60.i686.rpm
modwafexceptions-9.70-322.gd203205.rb13.i686.rpm
modwhatkilledus-2.01-0.258193062.g46092ac.rb61.i686.rpm
navl-tools-4.6.0.50-0.316899012.g8b86fac.rb3.i686.rpm
oculusd-1.0.0-0.322335831.gdf96f5d.rb6.i686.rpm
oculusd-dlz_oculus-1.0.0-0.322335831.gdf96f5d.rb6.i686.rpm
oculusd-highmem-1.0.0-0.322335831.gdf96f5d.rb6.i686.rpm
oculusd-lowmem-1.0.0-0.322335831.gdf96f5d.rb6.i686.rpm
perf-tools-3.12.74-0.327535988.gc5bb1a9.rb5.i686.rpm
python-PyYAML-3.12-1.0.317998409.gab3cfdd.rb2.i686.rpm
python-argparse-1.4.0-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-awscli-1.11.36-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-awscli-cwlogs-1.4.0-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-botocore-1.4.93-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-colorama-0.3.7-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-dateutil-2.6.0-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-docutils-0.13.1-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-futures-3.0.5-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-jmespath-0.9.0-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-ordereddict-1.1-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-pyasn1-0.1.9-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-rsa-3.4.2-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-s3transfer-0.1.10-1.0.317998409.gab3cfdd.rb2.noarch.rpm
python-simplejson-3.3.0-1.0.317998409.gab3cfdd.rb2.i686.rpm
python-six-1.10.0-1.0.317998409.gab3cfdd.rb2.noarch.rpm
red-unified-firmwares-9600-0.327764422.g822529a.rb2.i586.rpm
uma-9.70-1.gdb43019.rb2.i686.rpm
waf-ruledumper-1.0-0.318338720.g4e2e015.rb3.i686.rpm
xorg-x11-Xvnc-7.4-27.114.2.1931.gddf9adc5.rb1.i686.rpm
ep-reporting-9.70-39.gd06e9bb.rb5.i686.rpm
ep-reporting-c-9.70-158.g439c02e.rb4.i686.rpm
ep-reporting-resources-9.70-39.gd06e9bb.rb5.i686.rpm
ep-aua-9.70-9.gd6fadd4.rb4.i686.rpm
ep-awed-9.70-20.g6a8dbc3.rb2.i686.rpm
ep-branding-ASG-afg-9.70-37.gfc00437.noarch.rpm
ep-branding-ASG-ang-9.70-37.gfc00437.noarch.rpm
ep-branding-ASG-asg-9.70-37.gfc00437.noarch.rpm
ep-branding-ASG-atg-9.70-37.gfc00437.noarch.rpm
ep-branding-ASG-aug-9.70-37.gfc00437.noarch.rpm
ep-confd-9.70-588.g774f67a3f.i686.rpm
ep-confd-tools-9.70-470.gd129d9cd.rb11.i686.rpm
ep-init-9.70-9.g7905afa.rb4.noarch.rpm
ep-libs-9.70-12.g653adc3.rb4.i686.rpm
ep-localization-afg-9.70-37.gf4fd729.i686.rpm
ep-localization-ang-9.70-37.gf4fd729.i686.rpm
ep-localization-asg-9.70-37.gf4fd729.i686.rpm
ep-localization-atg-9.70-37.gf4fd729.i686.rpm
ep-localization-aug-9.70-37.gf4fd729.i686.rpm
ep-mdw-9.70-635.g15b10bc2.rb4.i686.rpm
ep-red-9.70-35.g94b4ce2.rb2.i686.rpm
ep-screenmgr-9.70-2.g224e1a8.rb3.i686.rpm
ep-tools-9.70-23.gb44eb11.rb3.i686.rpm
ep-tools-cpld-9.70-23.gb44eb11.rb3.i686.rpm
ep-up2date-9.70-15.g85f07d4.rb5.i686.rpm
ep-up2date-downloader-9.70-15.g85f07d4.rb5.i686.rpm
ep-up2date-pattern-install-9.70-15.g85f07d4.rb5.i686.rpm
ep-up2date-system-install-9.70-15.g85f07d4.rb5.i686.rpm
ep-webadmin-9.70-643.gbc4ac8ef3.i686.rpm
ep-webadmin-contentmanager-9.70-29.gf8059bd.i686.rpm
ep-chroot-httpd-9.70-18.gadbf8aa.rb2.noarch.rpm
ep-chroot-smtp-9.70-48.ga28fdc6.rb3.i686.rpm
chroot-httpd-2.4.18-10.g0c2e255.rb2.i686.rpm
chroot-ipsec-9.70-84.g84a2fe5.rb2.i686.rpm
chroot-reverseproxy-2.4.39-28.g4c96516.rb3.i686.rpm
ep-httpproxy-9.70-233.g5ff38467.rb3.i686.rpm
kernel-smp-3.12.74-0.327535988.gc5bb1a9.rb5.i686.rpm
ep-release-9.670-4.noarch.rpm
Related Posts
